TryHackMe - Simple CTF
- bobloblaw321
- May 6, 2020
- 3 min read
Updated: Mar 13, 2021
Welcome welcome! To my first walkthrough. We start with a relatively simple CTF room on TryHackMe: Simple CTF. https://tryhackme.com/room/easyctf
Scanning & Enumeration
As always, begin with enumerating the machine ports:
I used the (slightly modified) Threader3000 to get the open ports of the machine:

I then used nmap to scan those open ports found:
nmap -T4 -Pn -p21,80,2222 -A 10.10.206.93
Breaking down the command:
-T4: speed of nmap scan is 4/5 (personal preference of mine)
-Pn: skip pinging the machine being scanned (we already know the host is up)
-p21,80,2222: only scan the ports specified (the ones we found open)
-A: do an extensive scan on these ports
Enumerating Services
Port 21- ftp
From the nmap scan we see that the ftp port allows anonymous login, so we try that:
ftp 10.10.150.11
cd pub
get ForMitch.txt
exit
cat ForMitch.txtFrom the anonymous login, we have access to 1 file on the box, which informs us that there is password is weak, reused, and that there is probably a user name 'Mitch' (or some variation).
Port 2222- ssh
We see that ssh is available on port 2222, but ssh usually isn't too vulnerable unless we have credentials, so I leave it alone for now.
Port 80- http
A website being run on a port is usually a great place to visit on CTFs, so let's check that out:

Just a default page, so let's try to enumerate and see if we can find any hidden directories:
I used dirsearch to do this
python3 /opt/dirsearch/dirsearch.py -u http://10.10.206.93/ -e * -r
An interesting directory was found! Let's explore that.
Vulnerable WebApp
Navigating to the webpage, I have an extension called Wappalyzer which identifies webApp versions and as well as versions of services running on them:

Using that (as well as looking around the web page), we can see that this app is running CMS Made Simple. A google search for exploits on this service leads me to this:

After reading what the exploit does, I get retrieve it locally in hopes of obtaining some credentials:
searchsploit -m 46635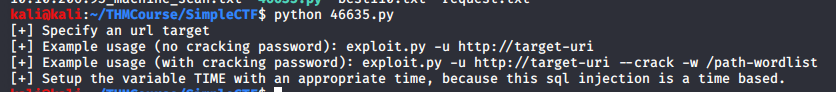
Running the exploit with no parameters shows you how to run it. We know the URL from our enumeration earlier, and I figure rockyou.txt (which comes preinstalled on kali) will be enough to crack any password we find.
python 46635.py -u http://10.10.206.93/simple/ --crack -w /usr/share/wordlists/rockyou.txtAfter running this and waiting for a bit, we obtain credentials!

Getting User
Now, these credentials we found are for the CMS site we saw earlier. But remember back to the beginning when I said ssh usually isn't useful until we have credentials. Well, now we have credentials so let's try that and see if some password reuse is going on!
I use medusa to check ssh validation. It's more useful for checking lists, but I'll show you the syntax anyway:

medusa -u mitch -p {password} -h 10.10.206.93 -M ssh -n 2222Breaking down the command:
-u: use a single username to test
-p: test a single password
-h: the host we are checking
-M: the module
-n: the port number (necessary since this box didn't have the default port 22 for ssh)
After checking with medusa we see that it's a success!
We ssh into the machine with the retrieved credentials
ssh mitch@10.10.206.93 -p 2222
And we get the user flag!
Privilege Escalation

After giving myself a normal shell with:
python -c "import pty; pty.spawn('/bin/bash')"we check if we can go get the root flag. As expected we get a Permission Denied.
So the first thing I like to check when it comes to Linux Privesc is what commands we can run as sudo:
sudo -l
Doing that, I see we can run vim as sudo! When you are in vim, you can run commands simply by prefacing them with '!'. I suspect we can spawn a root shell through this method:


sudo vimThen, inside of vim:
:!/bin/bashRunning vim with sudo and then spawning a shell, we can see that we are now root!

And we have access to the root flag!
That's all for now, thanks for reading :)
If you want to reach out for questions/feedback you can reach me on the TryHackMe discord server under the name B10b#9228!



Comments