TryHackMe - Buffer Overflows
- bobloblaw321
- Jun 10, 2020
- 3 min read
Updated: Mar 13, 2021
This write up will be a walkthrough of task 7 in the Buffer Overflows room on TryHackMe.
Task 7- environment setup
The goal for this task is to get the function to execute the 'special' function. Since we know we're working with buffer overflows, we are going to want to use gdb. Feel free to read up on that link if you are unfamiliar with gdb. So to get gdb up and running we do:
gdb func-pointer
We then run this set command, which sets gdb to use the environment to use the absolute path of any executables we run: AKA it means any exploit you make inside gdb will work outside of gdb after doing that.
set exec-wrapper env -u LINES -u COLUMNSFinding the return address
After we have our environment set up, we need to discover how many characters we need to user in order to overflow the buffer and cause a Segmentation Fault.
This clearly wasn't enough. Reading the C program that we're running, we see that the buffer is has a size of 14 (you should be able to recognize this from the previous task in the room). That means if we input more than 14, we should receive our desired SegFault.

Great! With 15 "A"s we can see that, as expected, the buffer overflows, and the program crashes.
The next thing we need to do is check how much we need to go in order to overwrite the return address:

Inputting 15 "A"s causes the rightmost character in the return address to be a "41" (the hexcode for 'A'). This means we have successfully started overwriting the return address! We must then check how much space we have in the return address to overwrite:

As we can see, sending an input of 20 "A"s overwrites the return address with all "41"s (the hex conversion of 'A'). Meaning, we have successfully overwritten the return address! In the next one, overwriting it with 21 "A"s causes the return address to no longer be overwritten and redirect somewhere else, meaning we went too far! That means we then have 6 bytes with which to overwrite the return address (20-14=6).
Overwriting the return address with the Special Function
We now have all the pieces set up in order to return to the special function, except one: the address of the special function! To find this, inside of gdb we can find it like so:
disassemble special
Great, from the first line, we see that the function begins at '0x0000000000400567'. So what we need to do next is overwrite the return address with what we've found!
As was mentioned earlier in the room, the architecture determines the endianess of the memory. We're dealing with little endian, and so the memory location we actually need to write, written in little endian, is:
\x67\x05\x40\x00\x00\x00We need to convert what we've found to ASCII in order to pass it in to our function:
**DISCLAIMER**
I did this a long time ago and have been too lazy to fix it, but basically, the way you should really do it is enter it into the function using backticks (`) or something along those lines with the actual hex. You should not convert it to ASCII and then paste it back in, as I do here (ah, to be young).
Reach out on Discord (handle on the bottom of the post) if you have trouble with this part, sorry for the confusion!

Passing our new return address to where we want to overwrite in our function:

AAAAAAAAAAAAAAg^E@And we've successfully overwritten the special function!
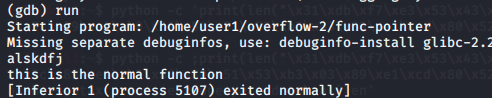
Also, as promised:

The function worked outside of gdb as well, due to the environment variables set earlier.
Try to execute the 'other' function to make sure you have a solid understand for what just happened.
Remember, this stuff is super challenging, don't be scared to take it slowly, at first.
That's all for now, thanks for reading :)
If you want to reach out for questions/feedback you can reach me on discord under the name B10b#9228!



Comments